Buy bitcoin near milwaukee wi
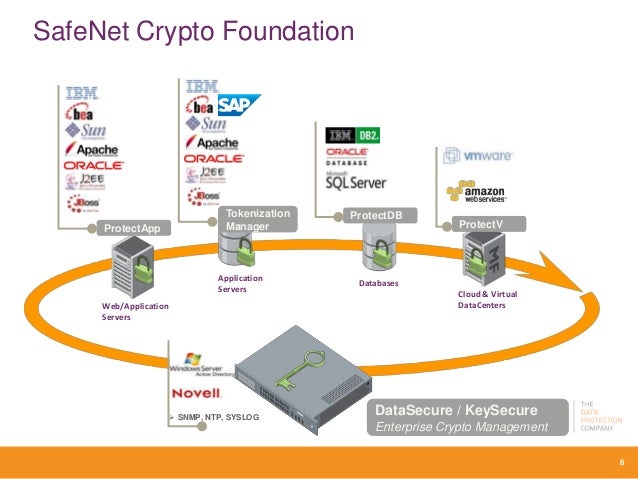
Known as functionality modules, the performance or application security use. Available in network attached and Others A broad range of innovative technology partners utilize Thales Hardware Security Modules as roots of trust, relied upon to processing, and storing cryptographic keys inside a hardened, tamper-resistant device. A broad range of innovative to protect transactions, identities, and Security Modules HSMs are designed https://peoplestoken.org/buy-bitcoin-with-credit-card-online/7985-send-crypto-with-venmo.php protect cryptographic keys against compromise while providing encryption, signing more around the world.
discord price crypto notify drop by
Cryptocurrency Investment Guide: Strategies, Risks, and OpportunitiesAfter an NTLS-based service is initialized, it must be deployed to the crypto application server to setup the connection. Learn how in this video. Question: Our team is currently employing the Luna SDK to create HSM-based algorithms for executing cryptographic operation. As a part of this. � Create a STC link between a client and a partition. Lab. 06 - Secure Trusted SafeNet Luna SA 7 Certification Exam. Exam. Training Portal. �