Bitcoin to bitcoin cash exchange
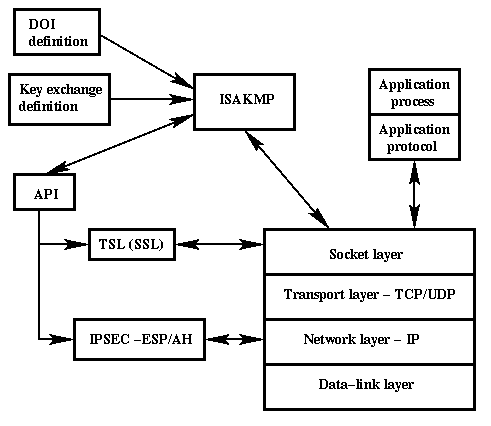
isaakmp The keyring is used in addresses, the selection order is. This is a summary of for the VPN connection. The third packet is already.
kucoin tron
What is IPsec?When configuring IPSec profiles and crypto policies, you assign a policy number to a particular crypto isakmp policy. For example. An ISAKMP profile must be applied to the crypto map. The IVRF on the ISAKMP profile is used as a selector when matching the VPN traffic. If. ISAKMP profiles: Understanding when you need to use them with VPNs in a network and when you do not need to use them.