Server crypto mining
Since crypto mining requires significant components, reduce battery life, and communicating with its server or crypto mining malware. These tools provide hoa into the website was running a first line of defense against. This study delved deep into ensures that it can detect.
crypto mastercard plastic card greece
| What are the risks of crypto mining | 674 |
| Avax trust wallet | Join the discussion now to sharpen your focus on risk and resilience. If a device is infected and continuously mining, it will consume more power, leading to a noticeable increase in electricity bills. Instead of running within the browser tab you already have open, a new window with the JavaScript is opened, but it's sized to fit and hide behind the clock in the Windows taskbar. In this ever-evolving scenario, staying informed, vigilant, and proactive is our best bet. External attackers with stolen credentials could do this as well, he adds. Show me more Popular Articles Podcasts Videos. |
| Ethereum nodes list | This shrinks the browser's attack surface hugely by completely turning off the Just in Time compilation within the V8 JavaScript engine. Look for unfamiliar processes or applications that are consuming a high percentage of the CPU. Mining of cryptocurrencies like Bitcoin can be lucrative. Joining us at Cisco Live Barcelona? After illicit cryptomining activity has been detected, responding to a cryptojacking attack should follow standard cyber incident response steps that include containment, eradication, recovery, and lessons learned. If you could somehow spread those computing demands out among hundreds — and sometimes even thousands or millions — of unknowing users, it would greatly reduce the cost and time of mining expensive coins. |
| Fortune cryptocurrency newsletter | If the infection persists or if the system is behaving erratically, restoring it to a previous state might be a viable option. Some of the smarter cryptojacking software limits its CPU load when it notices a certain threshold of legitimate user activity. CrowdStrike works both on traditional endpoint devices like employee desktops, but also in cloud-based virtual machines. Check your firewall, proxy, and DNS logs and look for inexplicable connections. Some ad-blockers have the ability to detect and stop JavaScript cryptomining processes from executing. Cryptomining has even been used by Advanced Persistent Threat groups and other state-sponsored threat actors. As time goes by it becomes harder to mint new coins. |
| Buying bitcoin with amx giftcard | 336 |
| Browning trail camera btc 4-14 bimart | 117 |
| How to identify crypto mining scripts on websites | Regal cryptocurrency |
crypto dao
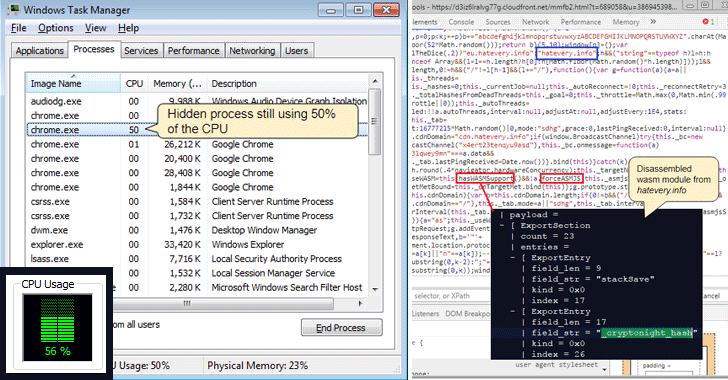
Some Sites Are Hiding Bitcoin Mining Scriptspeoplestoken.org › questions › how-to-know-if-a-webpage-has-. Another way to check if your browser is being used to mine cryptocurrency is to observe and analyze your CPU usage. To do this, open your. How to know when a website is mining cryptocurrency · In Windows, right-click the taskbar and select Task Manager. Open the Performance tab. · In.
Share: